Hello,
We are currently building an integration with Front that will utilize Webhooks. In the “Verifying Integrity” portion of the setup on step 4 it states to “Apply the hmac SHA256 algorithm using the token provided during webhook configuration as the key [output in base 64].”
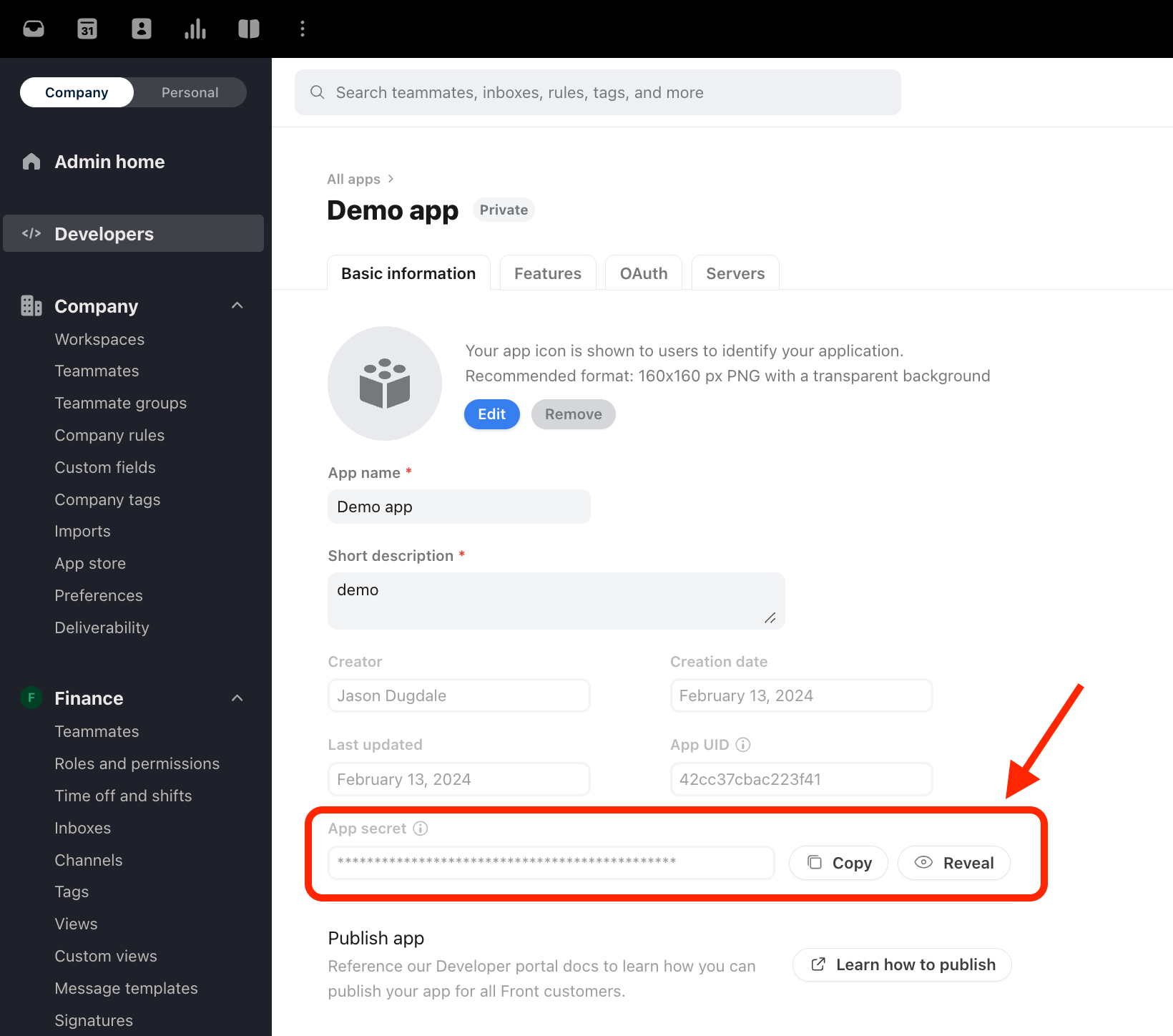
Where do we get this token?
The basic information tab only lists the App UID and App Secret while the OAuth tab only lists the Client ID and Client Secret. Are one of these to be used as the token or does it come from somewhere else.
Second, it also says to use the raw request body. I was hoping to confirm what the expected value of the raw request body should look like.
"{\"type\": \"sync\",\"authorization\": {\"id\": \"cmp_abc\"}}”
or
{\u0022type\u0022: \u0022sync\u0022,\u0022authorization\u0022: {\u0022id\u0022: \u0022cmp_abc\u0022}}
Thanks!